Smart Contract Security Best Practices
OnFinality, a multi-chain infrastructure provider, shares industry best practices for keeping your smart contracts secure.

OnFinality is a blockchain infrastructure platform that saves web3 builders time and makes their lives easier. We deliver easy-to-use, reliable and scalable API endpoints for the biggest blockchain networks and empower developers to automatically test, deploy, scale and monitor their own blockchain nodes in minutes.
In this article, we highlight security risks associated with smart contracts, and outline key best practices to help you mitigate potential vulnerabilities for a seamless development journey.
Let’s get started!
Contents
- Introduction
- What are Smart Contracts
- Types of Smart Contracts
- Smart Contract Best Practices
- Conclusion
- Additional Resources
Introduction
Smart contracts play a vital role in the Web3 ecosystem, enabling trustless transactions and decentralised applications. As smart contracts gain popularity, they bring along new security risks and threats, much like any other emerging technology. With blockchain technology constantly evolving, it’s important to be aware of these risks to stay ahead of the game.
What are Smart Contracts?
Smart contracts are self-executing agreements with the terms of the agreement directly written into code, enabling automated transactions and interactions on a blockchain. They work by executing predefined actions and conditions when specific criteria are met, eliminating the need for intermediaries.
Originating from Ethereum, the first blockchain platform to introduce smart contracts, these self-executing agreements have revolutionised the way transactions are conducted. Unlike Bitcoin, which lacked smart contract functionality, Ethereum paved the way for a new era of programmable and decentralised applications. Since then, numerous smart contract blockchains, such as Cardano, BNB Chain, and Solana, have emerged, with the integration of smart contract capabilities into Bitcoin now being pursued.
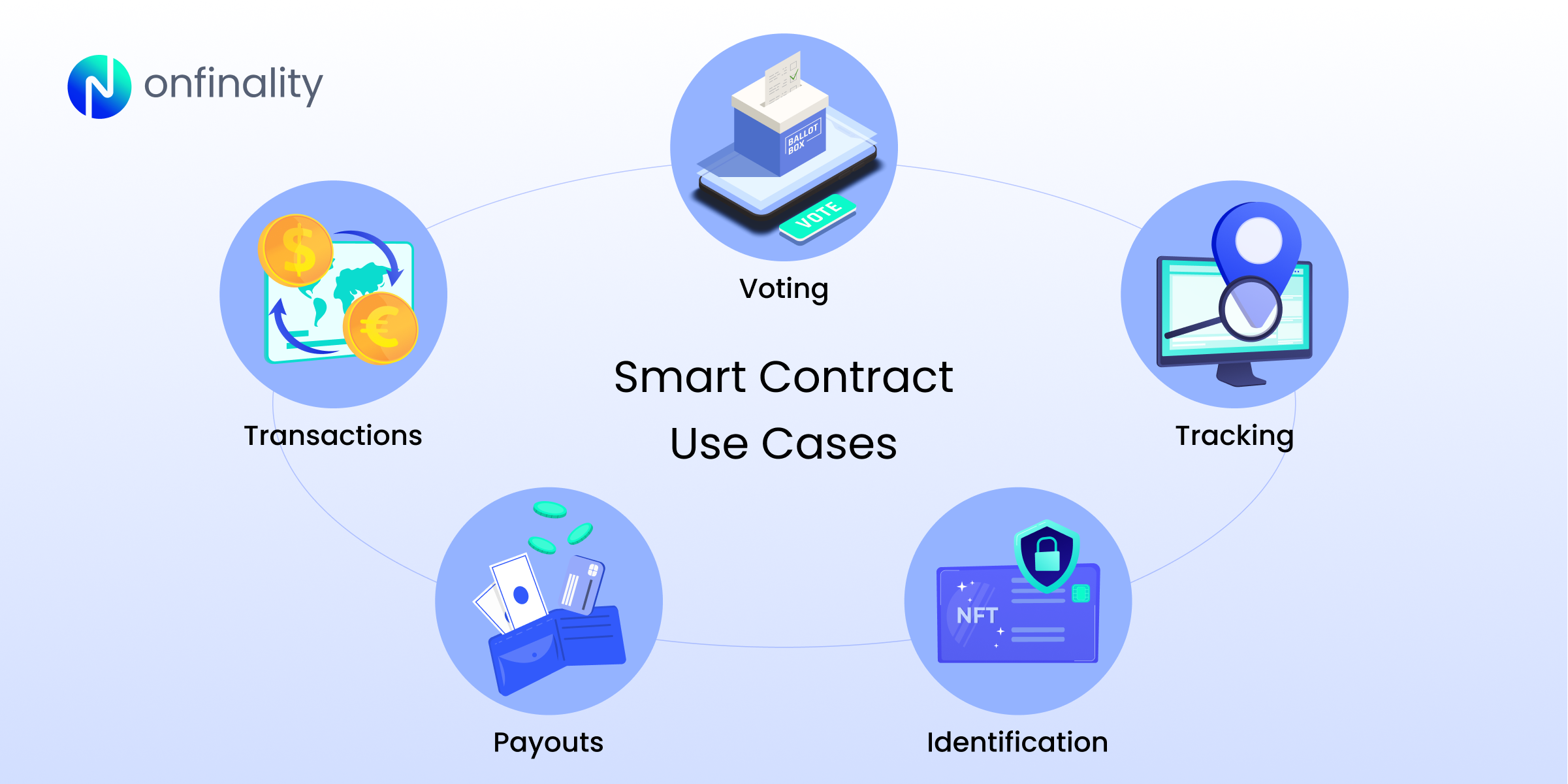
Smart Contract Use Cases
Smart contracts can be used in a wide range of industries for automated transactions and interactions, such as:
- Executing transactions on decentralised financial (DeFi) platforms
- Facilitating voting for governance within organisations (e.g. DAOs)
- Allowing efficient tracking of goods within the supply chain
- Automating claims and processing payouts for insurance platforms
- Enabling ownership verification for NFTs (Non-Fungible Tokens)
Smart Contract Best Practices
Below is a non-exhaustive list of smart contract best practices for secure development, offering guidance to developers in constructing dependable smart contracts. While these practices are valuable, it is important to note that they may not encompass all possible considerations or specific use cases that developers may encounter.

Solidity Code Review
Before deploying smart contracts, conducting thorough code reviews is essential. This process helps identify potential vulnerabilities, enhances reliability, strengthens security, meets compliance requirements, and ensures high-quality smart contract development. Moreover, understanding the Solidity language and its best practices is crucial for effective code reviews. Tools like MythX and Slither can assist in identifying vulnerabilities and provide insights into potential security risks.
Secure Development Practices
Adopting secure development practices while writing smart contracts greatly reduces the chances of introducing vulnerabilities. A modular design promotes code maintainability and reduces the attack surface. Proper input validation and error handling are also crucial to prevent unexpected behaviour. For example, integer overflow and underflow bugs can be mitigated by using the SafeMath library, which prevents arithmetic overflows.
External Dependencies
Smart contracts often rely on external contracts or make external calls, introducing potential security risks. Developers must exercise caution when interacting with external dependencies. Verifying and auditing external contracts is crucial to ensure their authenticity and security.
For example, in a decentralised finance (DeFi) protocol that interacts with an oracle to fetch external data, conducting audits on the oracle contract can help mitigate risks associated with data manipulation or unauthorised access. By carefully managing external dependencies, developers can enhance the overall security of their smart contracts.
Access Control and Permission Management
Implementing robust access control mechanisms prevents unauthorised access to contract functions. Role-based access control is commonly used to manage permissions effectively. For instance, a multi-signature wallet smart contract may require multiple authorised parties to approve transactions. By employing the principle of least privilege, the contract’s functionality is limited to authorised users, reducing the potential attack surface.
Secure Deployment and Upgradability
Deploying smart contracts securely is crucial to ensure the integrity of the deployed code. Validating the contract’s bytecode and verifying the authenticity of the deployment process are essential steps. Additionally, planning for upgradability is crucial for long-term contract maintenance. Implementing proxy contracts and utilising upgradeability patterns, such as the Transparent Proxy pattern, enable seamless upgrades while maintaining the contract’s security and integrity. OpenZeppelin provides a widely-used library for secure contract deployments.
Continuous Monitoring and Auditing
Continuous monitoring and auditing are vital for detecting potential security breaches or anomalies in smart contracts. Monitoring tools and techniques can provide real-time insights into contract behaviour, allowing for timely response to security incidents. Regular security audits conducted by external experts can help identify vulnerabilities and provide recommendations for improvement. For example, auditors may uncover issues like improper input validation or insecure access control, enabling you to rectify them before attackers exploit them.
Conclusion
Smart contract security is of paramount importance in the Web3 ecosystem. By following these best practices, you can significantly reduce potential vulnerabilities and ensure the integrity of your smart contracts.
By staying updated on security practices, leveraging industry tools, and conducting regular audits, we can all play a part in fostering a safer and more resilient Web3 future.
Additional Resources:
- Solidity documentation: Official language documentation for writing smart contracts.
- MythX: Security analysis platform for smart contracts and Ethereum code.
- Slither: Static analysis framework for detecting vulnerabilities in Solidity code.
- OpenZeppelin: Library for secure smart contract development and deployment.
- Security Auditors: Engage with reputable security auditors to review smart contract code and identify potential vulnerabilities. E.g. Trail of Bits, ConsenSys Diligence, Quantstamp
You may also be interested in:
- How OnFinality helps you manage security risks on your API endpoints
- Understanding the security functionalities of web3 wallets
Build Smarter with OnFinality. 😎
About OnFinality
OnFinality is a blockchain infrastructure platform that saves web3 builders time and makes their lives easier. OnFinality delivers scalable API endpoints for the biggest blockchain networks and empowers developers to automatically test, deploy, scale and monitor their own blockchain nodes in minutes. To date, OnFinality has served hundreds of billions of RPC requests, supports over 90 networks including Avalanche, BNB Chain, Cosmos, Polkadot, Ethereum, and Polygon, and is continuously expanding these mission-critical services so developers can build the decentralised future, faster!
